
Cloud Data Security
& Compliance
for Electronics
Development
Secure and elevate electronics design
collaboration with advanced cloud
security and compliance tools
collaboration with advanced cloud
security and compliance tools
Summary
Electronics design teams depend on robust security measures and compliance tools that safeguard intellectual property while supporting efficient collaboration.
While basic security measures exist in many design environments, they are not enough to keep a comprehensive design process safe. Cloud data security and compliance capabilities have evolved into a complete system that connects teams, protects data, and enables compliance with regulatory standards from initial design through production. All of these come with advanced encryption, access management, and real-time monitoring capabilities.
This cloud data security and compliance guide dives into everything IT security professionals and engineering managers need to know about electronics design data protection and the cloud, from fundamentals to advanced strategies for managing complex projects and cross-team collaboration.
Cloud data protection is the starting place for controlling access, streamlining collaboration, and maintaining design data integrity; as such, it needs to be configured and managed throughout a product's lifecycle. This guide provides an overview of how successful design teams implement cloud security and compliance, as well as how these processes impact team productivity and regulatory compliance.
What's the Difference Between Data Security and Compliance?
Security and compliance are distinct yet interconnected aspects of protecting your valuable intellectual property in the electronics design process. Understanding the difference will help you safeguard your design data.
Security
Security refers to the protective measures implemented to shield electronics design data from unauthorized access, breaches, theft and other malicious activities. It encompasses the tools, technologies and practices that protect intellectual property from both external and internal threats. Security is fundamentally about preventing unwanted access to your data and ensuring its integrity throughout the design process.
Compliance
Compliance relates to upholding established standards, regulations, and requirements set by industry bodies, governments, or internal policies. It's about meeting predetermined criteria that demonstrate your organization has implemented the necessary controls to protect sensitive information.
Security is the actual protection, and compliance is the demonstration and documentation of protection.
The relationship between the two is symbiotic:
- Strong security measures help you achieve compliance
- Compliance frameworks provide structured approaches to implementing security
- Both are necessary for a comprehensive approach to data protection
For electronics design teams, this distinction matters because different industries have varying compliance requirements. Defense contractors may need to meet CMMC or ITAR compliance requirements, medical device manufacturers must comply with FDA and EMA regulations, and companies handling European customer data need to adhere to GDPR standards.
Cloud-based tools offer significant cloud security compliance advantages by providing built-in controls and documentation capabilities that streamline these compliance processes as they maintain strong security.

Cloud vs On-Prem: Which Is Right for You?
When it comes to securing your electronics design data, one of the most fundamental decisions is choosing between cloud-based and on-premises security solutions. Each approach offers distinct advantages and considerations that can significantly impact your team's productivity, security posture, and compliance capabilities.
On-Premises Security: Traditional Control
On-premises security puts your data and security infrastructure entirely within your organization's physical control. Your team manages dedicated servers, hardware security modules, and all associated security infrastructure within your facilities.
Advantages:
- Physical control over all IT infrastructure containing your design data
- No reliance on internet connectivity for access to local files
- Complete customization of security configurations to your specifications
- Potentially beneficial for specialized compliance scenarios with strict data residency requirements
Challenges:
- Requires significant investment in hardware and security infrastructure
- Demands specialized in-house security expertise for maintenance and updates
- Limited geographic redundancy increases vulnerability to localized disasters
- Scales poorly as team size and project complexity grow
- Security updates require manual implementation, often leading to delays
- Remote collaboration typically requires complex VPN configurations
Cloud Data Security: Advanced Protection
Cloud-based data security leverages specialized providers' expertise and infrastructure to protect your design data, typically delivering enterprise-grade security at a fraction of the cost of building equivalent systems in-house.
Advantages:
- Advanced encryption methods with state-of-the-art protection protocols
- Geographic redundancy across multiple secure data centers
- Centralized security management with comprehensive access controls
- Automated updates and security patches without disruption
- Detailed activity logs and audit trails for tracking access
- Simplified secure collaboration for distributed teams
- Lower total cost of ownership for most organizations
- Rapid scalability to accommodate growing teams and projects
- Superior disaster recovery and business continuity capabilities
Challenges:
- Requires internet connectivity for real-time collaboration
- Less direct physical control over infrastructure
- Requires careful vendor evaluation for compliance needs
Making the Right Choice
For modern electronics design teams, the switch to cloud solutions increasingly depends on specific requirements:
Team Distribution
Globally distributed teams benefit significantly from cloud solutions that support secure collaboration without complex networking.
Budget Constraints
Cloud solutions typically offer enterprise-grade security with predictable subscription costs rather than large, uneven capital expenditures.
Compliance Requirements
While both solutions can address compliance needs, cloud providers increasingly offer specialized compliance certifications and documentation.
Technical Resources
Organizations without dedicated security specialists often achieve better security outcomes with cloud solutions that provide managed security services.
Many organizations are finding that a cloud-based approach to security delivers the optimal balance of protection, cost-effectiveness, and collaboration for electronics design teams. It also offers purpose-built security features that address the unique requirements of PCB design data and collaborative workflows.
For others, the most successful approach combines cloud-based security with appropriate offline capabilities. This allows teams to continue working even during internet disruptions–while still maintaining strong security controls.
The Benefits of Cloud Collaboration Tools vs the Old Way
Electronics design teams have traditionally faced a challenging dilemma: creating an effective collaboration solution while maintaining robust security controls. The conventional approach relies on siloed systems, restricted access, and complex file-sharing protocols that often impede teamwork in the name of security. Cloud collaboration tools represent a paradigm shift in this landscape, offering a solution that simultaneously enhances security and productivity.
Enhanced Cloud Data Security Through Centralization
Traditional design environments disperse data across local workstations, shared drives, and email attachments, making a larger surface area to secure. Cloud collaboration platforms consolidate your design data into a centralized, secure environment with:
- Comprehensive encryption both in transit and at rest
- Unified access controls applied consistently across all design assets
- Real-time monitoring for suspicious activities or unauthorized access attempts
- Controlled sharing that maintains security when collaborating with partners
- Detailed audit trails documenting access and modification
This centralization significantly reduces vulnerabilities compared to traditional file-sharing methods and enables security teams to implement stronger protections around a single controlled environment.
Mitigating Growing Cyber Threats
The threat landscape for electronics design teams has grown increasingly dangerous. According to cybersecurity research, the financial implications of cyber incursions are staggering. In 2025, the cost of cybercrime is projected to hit $10.5 trillion annually and shows no sign of slowing down. (Yes, that’s trillions, not billions.) The manufacturing industry has been particularly affected, with ransomware attacks more than doubling in recent years.
High-profile attacks continue to demonstrate vulnerabilities across sectors. For example, Communications & Power Industries (CPI), which serves the US Department of Defense and DARPA, experienced a ransomware attack that encrypted their data and led to a widespread system shutdown affecting thousands of computers. Despite general advice against paying ransoms, CPI was forced to pay $500,000, highlighting the dire circumstances companies face during such breaches. Similarly, Semikron, a German power electronics manufacturer with 3,000 employees across 24 subsidiaries globally, suffered a cyberattack resulting in partial encryption of their IT systems and files.
Cloud security platforms help address these threats through:
- Continuous security updates and patches without disrupting workflows
- Advanced threat detection utilizing artificial intelligence and pattern recognition
- Automated backups enabling rapid recovery from ransomware attacks
- Geographic redundancy that protects business continuity even during localized disasters
- 24/7 expert security monitoring for emerging threats
Streamlined Compliance Management
Regulatory compliance requirements continue to evolve and expand, creating significant administrative burdens for electronics design teams. Cloud collaboration tools simplify compliance through built-in controls aligned with major regulatory frameworks and automated documentation capabilities. They ensure consistent application of security policies across all design data while providing simplified auditing with comprehensive activity logs, ultimately reducing the administrative overhead needed to maintain compliance.
Enabling Secure Collaboration Without Boundaries
Cloud collaboration tools transform productivity by removing barriers while upholding strong security protections. They allow teams to access designs securely from anywhere, simplify onboarding processes, and enable controlled sharing with external partners. Teams benefit from real-time design reviews with managed stakeholder access and robust version control that prevents conflicts and protects data integrity throughout the collaborative process.
Cost Optimization Through Shared Resources
Data security in the cloud delivers significant cost advantages over traditional approaches by offering:
- Elimination of expensive on-premise security infrastructure
- Reduced need for specialized security personnel
- Predictable subscription-based pricing aligned with actual usage
- Minimized downtime and business disruption from security incidents
- Lower environmental impact through shared resources
Real-World Impact
The move to cloud collaboration tools delivers measurable benefits for electronics design teams. Improved collaboration reduces design cycle times, while significantly reducing the risk of intellectual property theft. Teams gain improved visibility into design progress and project status, enhance their adaptability to evolving security threats, and build greater resilience against disruptions ranging from cyber attacks to natural disasters.

Best Practices for Securing Cloud-Based Development Environments
Transitioning a design team to a cloud-based development environment requires thoughtful implementation. The following best practices will help your organization protect your intellectual property while promoting efficient collaboration.
Establish Robust Cloud Data Protection Measures
Cloud security ultimately centers on protecting your valuable intellectual design property.
- Ensure data encryption at rest and in transit using industry-standard methods
- Implement secure file-sharing processes for collaboration with external partners
- Establish version control and backup procedures to prevent data loss
- Create data retention and deletion policies aligned with business requirements
Monitor and Respond to Security Events
Effective security requires constant vigilance and the ability to respond quickly to potential threats.
- Implement comprehensive logging of all system and user activities
- Integrate with Security Information and Event Management (SIEM) tools
- Establish automated alerts for suspicious activities
- Create and test incident response procedures for potential security breaches
- Conduct regular security reviews to identify and address emerging risks
Manage Third-Party Risk
Cloud environments often involve multiple providers, each requiring appropriate security scrutiny.
- Conduct thorough vendor security assessments before implementation
- Review vendor compliance certifications relevant to your industry
- Establish security requirements in vendor contracts with clear responsibilities
- Perform periodic reassessments of vendor security practices
- Develop contingency plans for potential vendor security incidents
Plan for Business Continuity
Cloud environments offer superior resilience but still require robust continuity planning.
- Test backup and restoration capabilities regularly
- Create disaster recovery procedures specific to cloud environments
- Establish alternate access methods for critical operations during outages
- Document recovery time objectives for different systems and data
- Conduct periodic tabletop exercises to validate continuity plans
With thoughtful implementation of these best practices, electronics design teams can create comprehensive and collaborative cloud development environments that deliver superior security and align controls with specific business requirements and risk profiles.
Check Our Education Hub!
Free Webinars, Extensive Courses, and Much More Available to You.
Data Security and Compliance Tools
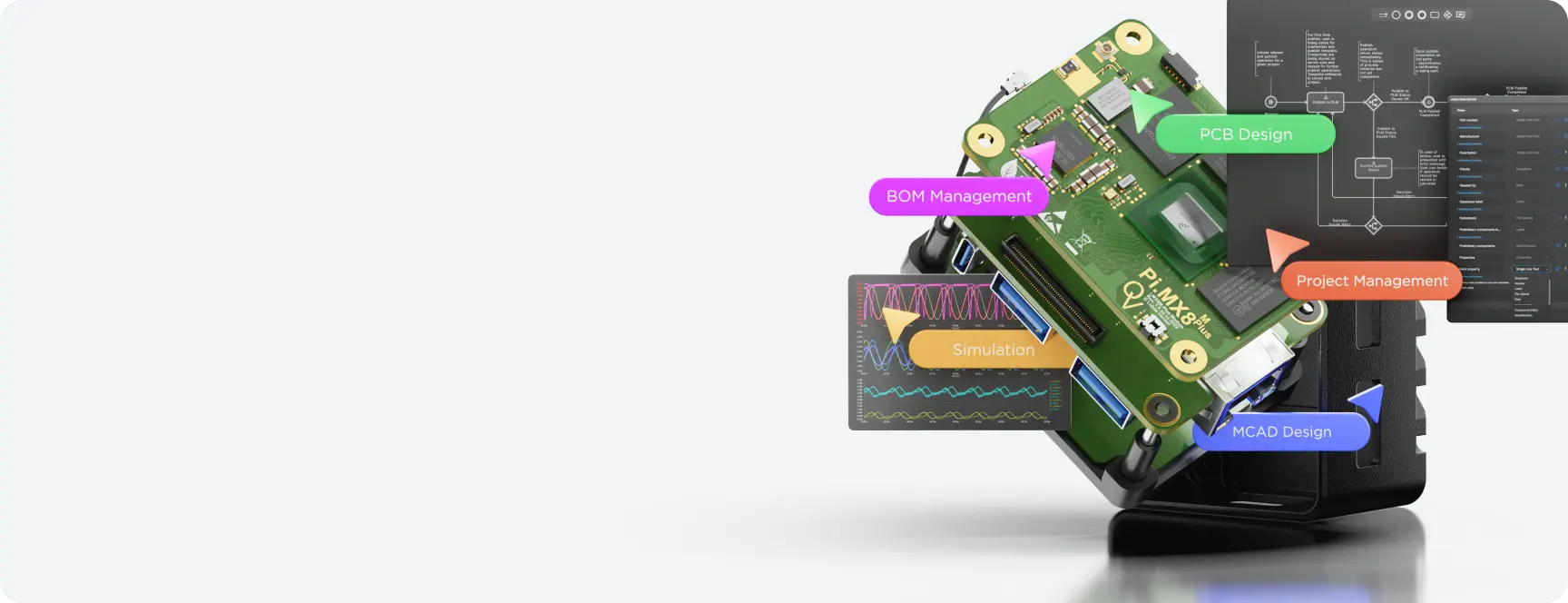
Real protection requires specialized tools for cloud-based collaboration. The Altium 365 cloud platform offers the Organizational Security Package with integrated tools that bridge the gap between robust security and efficient collaboration.
Cloud Infrastructure Security
The foundation of cloud security begins with the underlying infrastructure that hosts your design data.
- Multi-region deployment provides geographic redundancy across independent data centers to ensure availability and performance while maintaining appropriate data residency.
- Security-hardened infrastructure includes industry-leading cloud providers (like AWS) with comprehensive physical and network security.
- Vulnerability scanning identifies and addresses potential weaknesses before they can be exploited.
- Third-party penetration testing validates security effectiveness through simulated attacks.
The Altium 365 cloud platform employs a distributed architecture across multiple AWS regions with multi-availability zone storage services. This approach eliminates single points of failure while ensuring data remains accessible even during localized disruptions. The platform is built with security-driven development practices that include extensive architecture reviews, dependency scanning, code reviews, and dynamic application security testing.
Monitoring and Cloud Security Compliance Tools
Maintaining visibility into system activity is essential for both security and compliance purposes, including:
- Comprehensive event logging to track user actions and system events.
- SIEM integration API to connect with existing security information and event management systems.
- Automated compliance reporting to simplify regulatory documentation.
- Real-time alerting for unusual or suspicious activities.
These capabilities provide the visibility needed to detect potential security issues early while generating the documentation required for compliance audits.
Integrated Collaboration Tools with Built-In Security
Beyond infrastructure and access controls, modern cloud security solutions incorporate specialized applications that maintain security throughout the design workflow.
- Design review applications accelerate the review process while maintaining security controls. These tools track feedback in real time, monitor reviewer progress, and create permanent records for audit.
- Project management integration with Jira synchronization maintains security while streamlining task management. Bi-directional synchronization between design and project management platforms eliminates manual updates across systems and reduces errors.
- Event monitoring tools track detailed information for each system event, providing essential visibility for both security monitoring and compliance documentation.
The transition to cloud-based security represents a shift in how electronics design teams protect their intellectual property. Organizations that embrace this approach gain enhanced protection and improved resilience against disruptions, streamlined compliance processes, and the ability to collaborate securely across geographic boundaries.
As the threat landscape continues to evolve, cloud security platforms provide the agility to stay ahead of emerging risks while supporting the collaborative workflows that drive innovation in electronics design.
Recommended Reading

Whitepaper
Altium 365 Security Approach and Practices
Take an in-depth look into Altium 365’s security architecture.

Webinar
The Anatomy of IT Compliance
Explore practical strategies for safeguarding your intellectual property.

Article
Why You Should Prioritize Cloud Data Security
Discover why cloud security provides superior protection in today’s threat landscape.
Frequently Asked Questions
Cloud security leverages specialized providers' infrastructure to deliver advanced protection, including geographic redundancy, continuous updates, and centralized management. On-premises security relies on locally maintained hardware and software, providing physical control but requiring greater investment in infrastructure and expertise. Most organizations now find that cloud security offers superior protection with a lower total cost of ownership.
Cloud security platforms typically include built-in compliance controls, automated documentation, and comprehensive audit logging. These capabilities simplify adherence to industry standards and regulatory requirements by providing consistent application of security policies and simplified reporting for audits. Leading cloud platforms maintain certifications for major compliance frameworks, reducing the administrative burden of documentation.
Depending on your industry, important certifications include SOC 2 Type 2 for general security practices, ISO 27001 for information security management, GDPR compliance for handling European data, and industry-specific certifications like HIPAA for healthcare or ITAR for defense electronics designs. Check if your provider maintains current certifications relevant to your regulatory environment.
Cloud security platforms enable secure external collaboration through controlled sharing with precise permissions, comprehensive audit logging of all access, encryption of shared data, and the ability to revoke access immediately when no longer needed. The security of cloud storage and collaboration solutions provides significantly better protection than traditional file-sharing methods when working with contract manufacturers, clients, or other external stakeholders.
Cloud security platforms typically implement geographic redundancy across multiple data centers, automated backup systems with point-in-time recovery capabilities, and comprehensive disaster recovery protocols. These measures ensure business continuity even during significant disruptions, with recovery times far superior to traditional on-premises approaches.
Yes, modern cloud data security and compliance solutions include secure integrations between design platforms and project management tools like Jira. These integrations maintain security through authenticated API connections and consistent access controls while ensuring that tasks, issues, and comments stay updated in both systems without compromising security.